In early 2025, major retailers like The North Face, Cartier, and Victoria’s Secret reported breaches that exposed customer email addresses through credential stuffing, misconfigured systems, and unauthorized backend access.
These incidents made it clear that email exposure isn't a minor issue; it's often the starting point for phishing, impersonation, and broader compromise. This article examines how these attacks unfolded, identifies where defenses failed, and outlines security measures that can be implemented to mitigate the risk of similar breaches in the future.
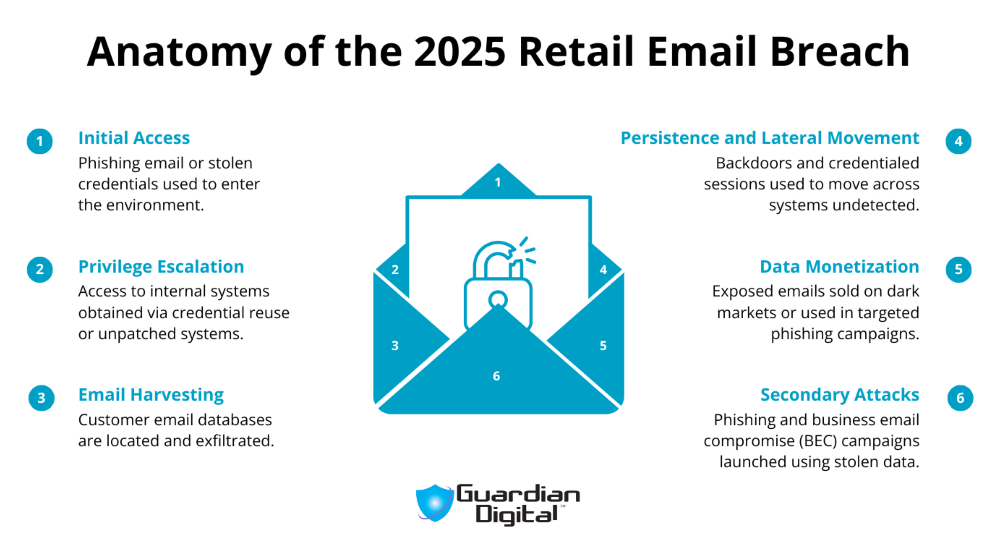
The 2025 Retail Breaches: Anatomy of the Incidents
Several major retail brands were targeted in early 2025 through a mix of credential-based attacks and unauthorized system access. In April, The North Face disclosed a credential stuffing breach that compromised customer account data.
Attackers used email/password combinations from earlier leaks to access accounts that lacked strong authentication protections. While payment details weren’t stolen, customer emails, names, and order histories were harvested.
Around the same time, Cartier confirmed a breach involving unauthorized access to customer data, including emails and personal identifiers, after a successful social engineering campaign against a backend service provider.
In May, Victoria’s Secret suffered a more disruptive breach that forced a temporary shutdownbreach that forced a temporary shutdown of its U.S. online shopping operations. The incident, which is still under investigation, involved the confirmed exposure of email-address-level customer data and highlighted weaknesses in core corporate systems.
These events highlight a growing trend: attackers are targeting retail brands with high customer email volumes and minimal visibility into email-based activity across their infrastructure. Attackers are prioritizing access to customer-facing systems with limited detection, weak credential policies, and incomplete API access controls.
How Infrastructure Gaps Enabled the Attacks
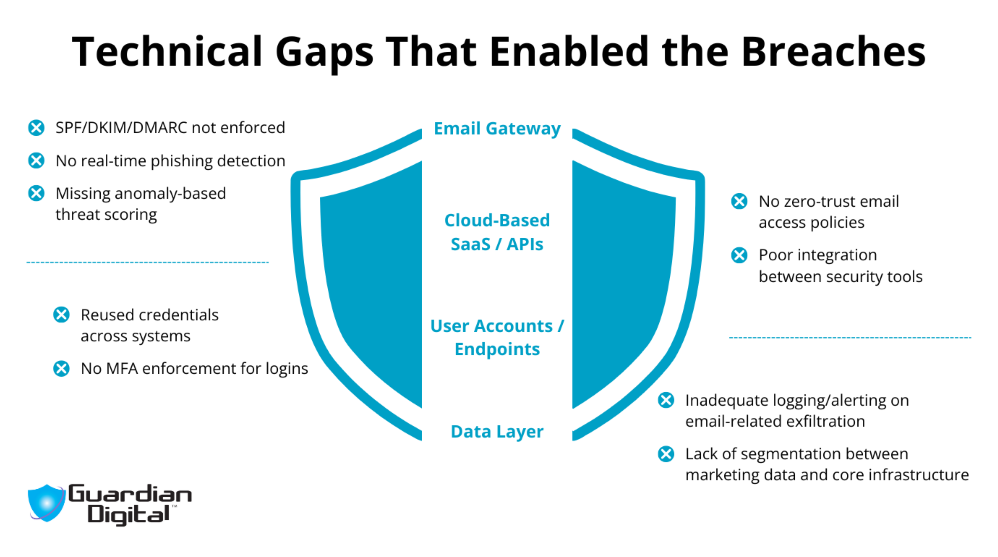
These breaches exposed systemic weaknesses that attackers repeatedly exploited. In The North Face incident, the absence of multi-factor authentication and poor login attempt throttling allowed automated tools to test thousands of credential pairs without resistance.
Cartier’s case involved inadequate session auditing and a lack of real-time monitoring, allowing unauthorized access to go undetected long enough for sensitive customer records to be pulled from internal systems. In both cases, the failure to detect behavioral anomalies early on provided attackers with the time and space they needed to operate undetected.
One of the most consistent technical gaps across these breaches was the weak enforcement of email authentication protocols. SPF, DKIM, and DMARC, which help verify sender legitimacy and reduce spoofing, were either misconfigured or applied too loosely to block forged messages.
Without strict email policies in place, attackers could exploit trust in brand email domains to launch phishing attacks following data exposure. These breakdowns, combined with a lack of real-time insights into email behavior or policy violations, made each breach more damaging than it needed to be.
Technical Risks of Exposed Emails
Once email addresses are exposed to a breach, the most immediate threat is phishing. Attackers often launch campaigns that mimic trusted services, prompting users to enter passwords or verify account details. These emails are often linked to cloned login pages that collect credentials in real-time. If users reuse passwords across platforms, attackers gain quick access to other systems.
Spear-phishing raises the threat even further. In these cases, attackers craft messages that appear to come from executives, vendors, or internal teams.
They rely on trust, familiarity, and urgency to push recipients into taking harmful actions, such as approving wire transfers or sharing sensitive internal information. This tactic doesn’t rely on technical exploits; it works when organizations don’t have strong controls on sender authentication or internal message verification.
Business email compromise (BEC) often builds on these earlier attacks. Once attackers gain access to internal email accounts either through phishing or credential reuse, they monitor communications to find opportunities for fraud.
Redirected invoices, fake vendor updates, and altered payroll instructions are all common outcomes. Since the emails originate from real accounts, detection becomes more challenging without behavioral analysis or automated flagging systems.
Broader Risks and Long-Term Impact
Email addresses are often used as usernames, which makes credential stuffing easier once those addresses are known. Attackers run automated scripts to test known email/password pairs across hundreds of services.
If multi-factor authentication isn't active and rate-limiting controls are weak, those scripts are highly effective. Many breaches escalate because accounts across unrelated systems are compromised within hours of the email leak.
Beyond logins, leaked emails are used to shape more complex attacks. When attackers combine an email address with previously breached data, they can craft custom payloads targeting specific platforms, especially cloud services.
SaaS platforms, such as Microsoft 365, Google Workspace, or Slack, are common targets because many organizations don’t thoroughly audit login activity or implement strict access controls.
User behavior also plays a significant role in determining the extent of a breach. Poor account hygiene, such as reusing passwords or failing to update credentials after exposure, provides attackers with long-term access. Most victims never realize their address has been used in multiple campaigns until it's too late.
Systems with integrated threat intelligence can help identify patterns early, especially when email filtering tools track emerging campaigns across various industries and infrastructures.
Attribution & Strategic Implications
There’s growing evidence that some of the retail breaches in 2025 were not random. Analysts have identified links between the tactics used and known behaviors from state-backed groups, particularly APT38 and Lazarus.
These groups have previously focused on financial theft and espionage, but their techniques are now appearing in campaigns against commercial targets. The use of advanced phishing kits, lateral movement across email infrastructure, and delayed data extraction suggest a level of planning that goes beyond standard cybercrime.
At the same time, many incidents still trace back to large-scale organized cybercriminal networks. These groups use widely available phishing kits and credential-stuffing tools to automate attacks at scale. Once they gain access to user emails or backend portals, they move quickly to extract valuable data or drop malicious payloads. What’s clear in both cases, whether it’s a state actor or a profit-driven group, is that attackers are becoming more deliberate in targeting systems where email access leads to broader compromise.
Why Retail Remains a Primary Target
Retail remains attractive due to the high volume of customer emails and often limited visibility into how those systems are accessed and utilized. Many of these companies manage large subscriber lists, run promotional campaigns through third-party platforms, and rely on cloud-based services that aren’t always well-integrated into security workflows. That leaves plenty of surface area for phishing, spoofing, or API abuse.
Resource limitations make the problem worse. Most retail organizations lack a dedicated security operations team, and their IT staff are typically stretched thin across infrastructure, compliance, and customer-facing applications.
Without a multi-layered approach to email protection or outsourced security built to manage phishing, spoofing, and behavioral threats, gaps start to form. Managed email security services that offer real-time monitoring, threat detection, and policy enforcement provide smaller teams with a more effective way to keep pace without adding unnecessary overhead.
Mitigation: Modern Email Security Recommendations
There are several consistent patterns in the breaches that occurred in 2025, which point directly to the kinds of protections that need to be in place.
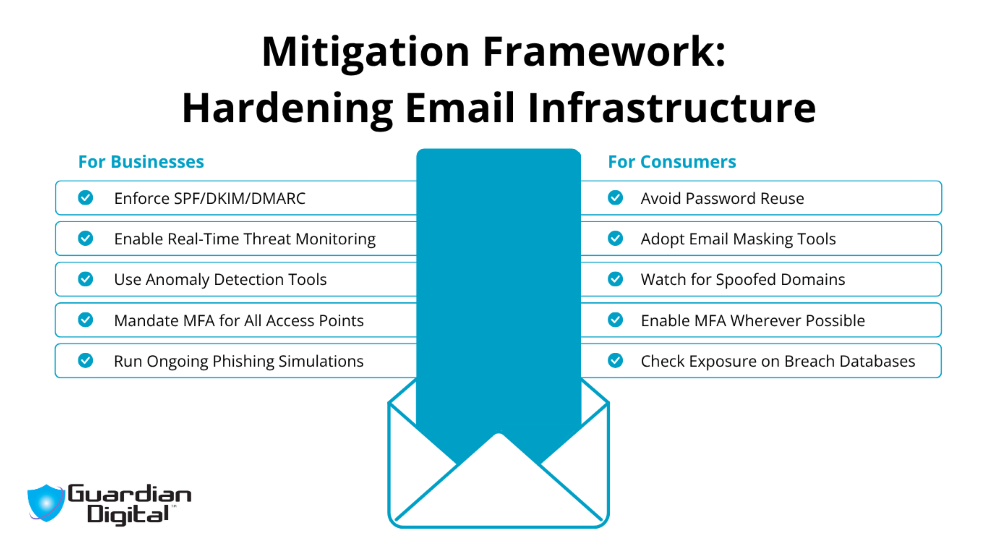
Most retail organizations would benefit from strengthening domain-level email authentication and investing in tools that detect suspicious behavior as it happens. These measures help block spoofing attempts and reduce the time attackers stay unnoticed.
- Apply SPF, DKIM, and DMARC with strict policies
Loose or missing configurations allow attackers to send spoofed emails using legitimate domains. Setting DMARC to "reject" and actively monitoring reports helps reduce this exposure. - Use real-time behavioral detection tools: Monitor for unusual login patterns, geolocation mismatches, and rapid data access from internal accounts. This level of visibility can significantly shorten response times and prevent ongoing attacks.
- Invest in phishing awareness and response training: Security tools can't catch everything. Regular training on identifying high-risk emails gives staff the knowledge to spot red flags before a compromise occurs.
- Adopt multi-layered filtering and access control models: Relying on a single security method creates gaps in protection. Combining spam filtering, link scanning, attachment sandboxing, and least-privilege access policies builds better coverage across email systems.
What Individuals Can Do Right Now
Even when organizations take email security seriously, users still play a significant role in protecting their data. Many attacks succeed because of reused credentials, weak passwords, or a lack of awareness about how exposed their information already is. Staying informed and implementing a few changes to how personal email is managed can significantly reduce risk.
Start with:
- Stop reusing passwords across services: Credential stuffing depends on this. Use a password manager to generate and store strong, unique credentials.
- Use email aliasing or obfuscation where possible: When signing up for services, use disposable or masked email addresses to limit how often your primary address is stored and potentially leaked.
- Check breach status regularly. Services like Have I Been Pwned enable you to monitor whether your email address has been exposed in recent data breaches. If it has, reset passwords immediately and watch for suspicious messages.
These steps don’t require technical expertise but can significantly reduce exposure when done consistently. Security tools do their part, but personal habits often decide how much attackers can do with the data they find.
Takeaway: Email Exposure Is the Weak Link
Exposed emails continue to be a common entry point in large-scale cyberattacks, leading to a range of consequences, from credential theft to internal fraud. The 2025 retail breaches showed how quickly attackers exploit weak email defenses when monitoring and enforcement are limited. Organizations that treat email as a primary threat vector and secure it with layered filtering, real-time detection, and strong policy controls are more likely to catch threats early. If your current solution lacks this level of visibility, Guardian Digital offers cloud-based email security designed to prevent phishing, spoofing, and account compromise before damage is done. Begin with a risk assessment or request a demo to see how it aligns with your environment.